InfoSec | Crypto Challenges | CarolinaCon 2017
Starter / Level 0:
At registration, we were given a slip of paper that had the crypto challenge starter printed on it. It read:
UVd4c0lHOW1JSFJvWlNCc1pYWmxiQzExY0NCd2FISmhjMlZ6SUdGeVpTQnNiM2RsY21OaGMyVWdiRE16ZEhOd1pXRnJJSGRwZEdnZ2JtOGdjM0JoWTJWekxpQkpaaUIwYUdWeVpTQmhjbVVnYzNCaFkyVnpJR2x1SUdGdUlHRnVjM2RsY2l3Z2NtVndiR0ZqWlNCMGFHVnRJSGRwZEdnZ1pHRnphR1Z6TGlCUGJtTmxJSGx2ZFNCb1lYWmxJSE52YkhabFpDQjBhR1VnY0hWNmVteGxJR1p2Y2lCaElHeGxkbVZzTENCemRXSnRhWFFnYVhRZ2RHOGdkR2hsSUhObGNuWmxjaUIzYVhSb0lIUm9aU0JtYjJ4c2IzZHBibWNnVlZKTU9pQm9kSFJ3Y3pvdkwyOXNaR2R5WldkbkxuZDBaaTg4YkdWMlpXeHVkVzArTHp4MWMyVnlhMlY1UGk4OFpteGhaejR1SUZSb1pTQnNaWFpsYkNBeElIQm9jbUZ6WlNCcGN5QjBhR0Z1YXpVd2JHUm5jak5uWnk0Z0lDQUsK
We noticed that the only characters represented in the string were A-Z, a-z, and 0-9, so we suspected that this may be the result of Base64 encoding. Base64 decoding the string resulted in the following:
QWxsIG9mIHRoZSBsZXZlbC11cCBwaHJhc2VzIGFyZSBsb3dlcmNhc2UgbDMzdHNwZWFrIHdpdGggbm8gc3BhY2VzLiBJZiB0aGVyZSBhcmUgc3BhY2VzIGluIGFuIGFuc3dlciwgcmVwbGFjZSB0aGVtIHdpdGggZGFzaGVzLiBPbmNlIHlvdSBoYXZlIHNvbHZlZCB0aGUgcHV6emxlIGZvciBhIGxldmVsLCBzdWJtaXQgaXQgdG8gdGhlIHNlcnZlciB3aXRoIHRoZSBmb2xsb3dpbmcgVVJMOiBodHRwczovL29sZGdyZWdnLnd0Zi88bGV2ZWxudW0+Lzx1c2Vya2V5Pi88ZmxhZz4uIFRoZSBsZXZlbCAxIHBocmFzZSBpcyB0aGFuazUwbGRncjNnZy4gICAK
Although shorter, the same set of characters is represented in the string output of the Base64 decoder, with the addition of the + symbol, so we suspected that this was also the result of Base64 encoding. Decoding a second time resulted in the following:
All of the level-up phrases are lowercase l33tspeak with no spaces. If there are spaces in an answer, replace them with dashes. Once you have solved the puzzle for a level, submit it to the server with the following URL: https://oldgregg.wtf/<levelnum>/<userkey>/<flag>. The level 1 phrase is thank50ldgr3gg.
That provided us several details regarding the challenge; notably, the challenge web site and how it operates. We visited https://oldgregg.wtf, registered our team name to receive a user key, and then proceeded to Level 1 by submitting the following URL:
https://oldgregg.wtf/1/41fa577c-687b-4b5d-af35-50396b070fda/thank50ldgr3gg
Level 1:
Upon arriving at the Level 1 web page, we were presented with this image:
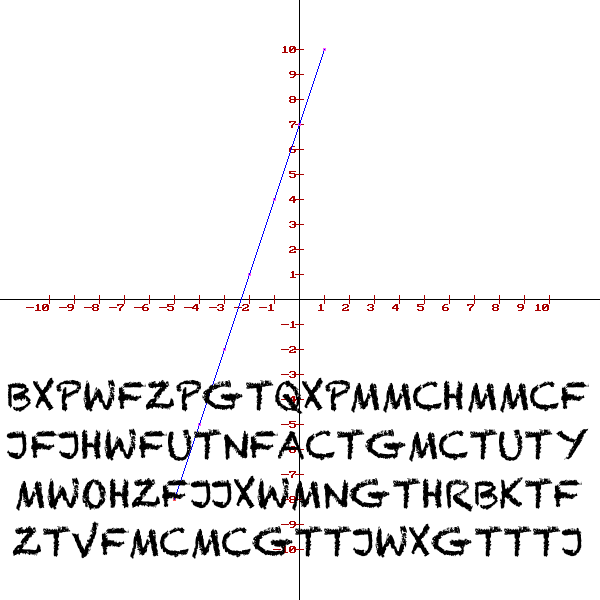
Seeing the graph of a linear function coupled with encoded text immediately indicated to us that the text was encoded using the Affine cipher. From looking at the graph, we were able to determine that the function was:
f(x) = 3x + 7
Having determined that, we were able to decode the text provided in the image. So the encoded text:
BXPWFZPGTQXPMMCHMMCF
JFJHWFUTNFACTGMCTUTY
MWOHZFJJXWMNGTHRBKTF
ZTVFMCMCGTTJWXGTTTJ
Deciphered to this text:
YOUFIGUREDOUTTHATTHI
SISAFINECIPHERTHENEX
TFLAGISSOFTCREAMYBEI
GEWITHTHREESFOREEES
We know from the Starter that the flags are all lower-case and the deciphered text tells us to replace all Es with 3s. So the flag becomes:
SOFTCREAMYBEIGE
softcreamybeige
softcr3amyb3ig3
So we proceeded to Level 2 by submitting the following URL:
https://oldgregg.wtf/2/41fa577c-687b-4b5d-af35-50396b070fda/softcr3amyb3ig3
Level 2:
Arriving at Level 2, we were presented with the following image:
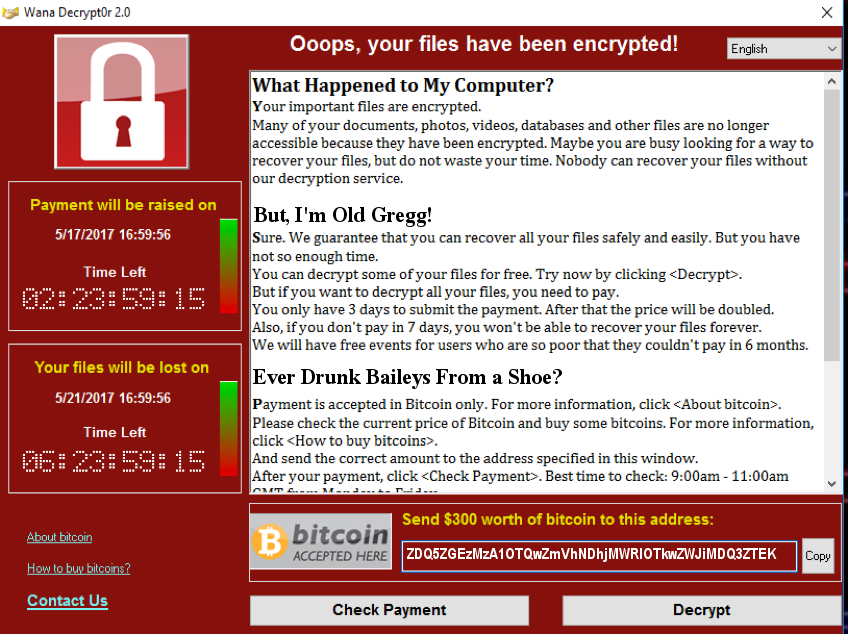
After examining the information in the image, our initial thought was that there was some relevant information at the displayed Bitcoin address. We quickly discovered that wasn't the case and began working on other ideas.
While looking for signs of steganography, we noticed that a series of ones and zeroes was appended to the end of the file data:
01010011011011110110110101100101011101000110100101101101011001010111001100100000011101000110100001100101011100100110010100100111011100110010000001101110011011110010000001100011011010010111000001101000011001010111001000100000011010010110111000100000011100000110110001100001011110010010111000101110001011100010000001110100011010000110010100100000011011100110010101111000011101000010000001100110011011000110000101100111001000000110100101110011001000000110100101101101001101000110001001101001011001110110011000110001011100110110100001100110001100010110111001100111011001010111001000101110
Converting the binary to ASCII resulted in this:
Sometimes there's no cipher in play... the next flag is im4bigf1shf1nger.
We then proceeded to Level 3 by submitting this URL:
https://oldgregg.wtf/3/41fa577c-687b-4b5d-af35-50396b070fda/im4bigf1shf1nger
Level 3:
The page for this level contained the following image for us:

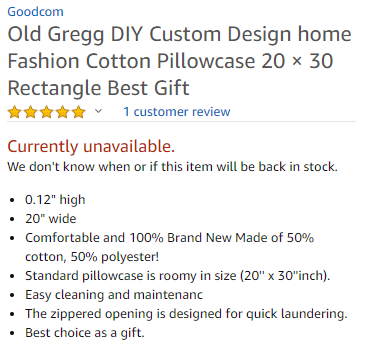
Being frequent Amazon shoppers, we thought the model ID in the image, B01-JZ10-ORS, resembled an Amazon ASIN (Amazon Standard Identification Number) with a couple of added hyphens. A quick web search revealed that this was accurate and a product was listed on Amazon with ASIN B01JZ10ORS and located here:
https://www.amazon.com/Custom-Design-Fashion-Pillowcase-Rectangle/dp/B01JZ10ORS
We immediately knew we were on the right track when we saw that the product was related to Old Gregg:

This was further reinforced when we saw that the product's lone review was submitted by Aaron Lint (@lintile), the person who created the challenge:
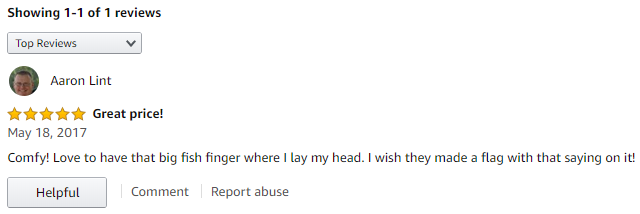
After reading through the listing, we couldn't find anything that was related to Old Gregg other than the product itself. We concluded that the flag phrase was the text written on the product: "Do Ya Love Me?" Based upon the instructions we'd received earlier, we tried the following variations for the flag phrase: d0y4l0v3m3, d0-y4-l0v3-m3, do-ya-love-me, and finally doyaloveme, which was the correct flag.
Thus, we submitted https://oldgregg.wtf/4/41fa577c-687b-4b5d-af35-50396b070fda/doyaloveme in order to proceed to Level 4.
Level 4:
When the page for this level loaded, we were presented with this text:
WOTNOIEP ASIEYU HECBUHSLVU HL T 1TOR NEFEATT E WTOK YTANEO 1LIOMU
Based upon the inconsistent spacing between the words, we suspected that this text was most likely the result of a Rail Fence Cipher. We used an increasing number of rails to try deciphering the text until the deciphered text made sense when the number of rails was set to four. In hindsight, that should've been our first try, since this was level four. The deciphered text was:
WERE YOU ON THE FENCE ABOUT THIS 1 LEVEL UP WITH LOOK AT MY S1TUATION
Removing all of the spaces and changing all letters to lowercase resulted in the following flag: lookatmys1tuation. So, we were able to reach Level 5 by submitting the following URL:
https://oldgregg.wtf/5/41fa577c-687b-4b5d-af35-50396b070fda/lookatmys1tuation
Level 5:
The page for level five displayed the following message:
0 -0-.'; ;3*1 :5? ,58 3. 1-†38 3221. $51 ,3. 4?; 0; )11‡) 20*1 :5? ,5?.- ;71 )1681; ;71 .1¢; 21¶12 *1: 0) ]73;673-550.0.‡:]3;18)
Neither of us being English majors, we missed the obvious clues this message contained and decided that this was just a weird substitution cipher. We resorted to a bit of brute-force substitution, cryptogram style, which eventually yielded the following result:
i didn't take you for an edgar allen poe fan but it seems like you found the secret the next level key is whatchadooininmywaters
Upon seeing the name Edgar Allen Poe in the deciphered message, I vaguely recalled a story, obviously written by Poe, that involved secret messages written in code. I'd read this back in high school, when all of the cool kids were reading Mr. Poe's works, so I had to search for the story on the web.
It didn't take long to discover that the story was titled The Gold Bug and the exact same enciphered text was used in the story. The cipher is called the "Gold Bug Cipher."
After feeling like total fools for not remembering this, we submitted the following URL to see Level 6:
https://oldgregg.wtf/6/41fa577c-687b-4b5d-af35-50396b070fda/whatchadooininmywaters
Level 6:
Upon arrival at the level six page, we saw the following image:
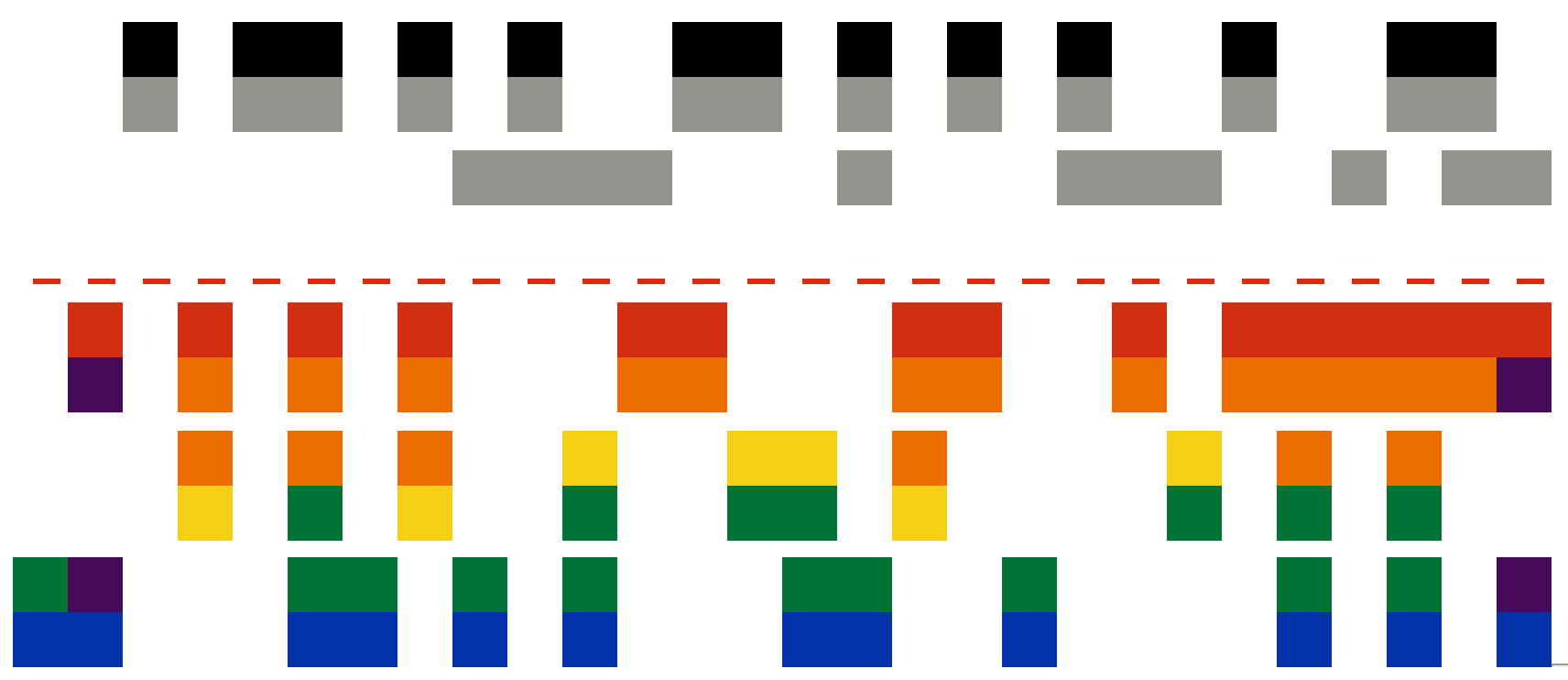
Deciphering the information hidden within this image took us quite some time. While we didn't spend the most amount of time on this level, it was definitely the next. In fact, this is the level where most of the contestants stopped:
We began examining the image for any patterns we could find, but kept arriving at nothing. We thought there was something important about the order and arrangement of the individual colors. After staring at this image and discussing it for hours, we went to Denny's to have dinner. Naturally, while we were there, we continued to discuss the problem before us. It was here that Jon mentioned two important things to led to our breakthrough.
First, in the bottom section, the color blocks appear in pairs. There are only two unique pairs of color blocks in each of the three rows of the bottom section.
Second, if the color blocks are uniquely paired in the bottom section, then the top section should also follow that convention. The image was most likely purposefully given a white background in order to mask some of the pairs in the top section.
After he made those statements, we discussed the odd placement of the grey blocks in row two of the top section. That row didn't appear like any of the other rows in the image. However, if the grey blocks were paired with white blocks, we wouldn't necessarily know that due to the white background. So, we made the assumption that the grey blocks were paired with white blocks.
At this point, I realized that we were seeing a graphical representation of a five-bit encoding scheme. Being an amateur radio operator who is enthusiastic about digital communications protocols, I immediately thought of the old Baudot Code. In order to confirm my suspicion, I searched the web for some resources to read about Baudot Code. Upon seeing an image of Baudot ticker tape, I knew we were on the right track:

After this confirmation, I searched the web for "baudot color blocks" to see what I could find. Interestingly, one of the top results was an article about the album cover for Coldplay's album X&Y. Upon viewing the album cover, I knew we were close to solving this level. Additionally, the search results contained some sites for enciphering text using Baudot Code color blocks (or Coldplay Code):
http://luthorien.altervista.org/Tools/baudot.htm
We used these sites to generate an image for the entire alphabet:
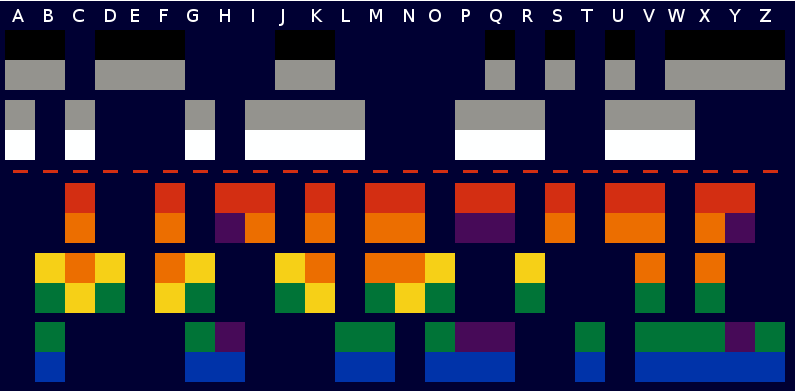
At this point, it was just a matter of matching each column in the image to a letter in our alphabet above. After doing this, we deciphered the following flag phrase: downstairsmixup.
So, we passed this great cryptochallenge barrier and made it to Level 7 by submitting this URL:
https://oldgregg.wtf/7/41fa577c-687b-4b5d-af35-50396b070fda/downstairsmixup
Level 7:
The level seven page greeted us with this interesting image:

We initially thought it was some type of cuneiform; however, that proved to be incorrect. After looking at images of various alphabets using Google Image Search, we stumbled upon the Dragon Alphabet from Skyrim:

After matching each symbol in the message to a Latin letter, we deciphered the flag phrase: nicemoderngentleman.
We proceeded to Level 8 with the following URL:
https://oldgregg.wtf/8/41fa577c-687b-4b5d-af35-50396b070fda/nicemoderngentleman
Level 8:
The level eight page presented this text to us:
2A 16 96 CE 04 F6 76 A6 04 B6 86 9E 04 16 86 6E A6 04 46 A6 A6 76 04 16 86 4E 26 04 2E F6 04 26 F6 34 04 46 AE 2E 04 2E 16 86 2E E4 CE 04 EE 16 9E 04 9E F6 AE 04 86 36 EE 86 9E CE 04 C6 16 A6 C6 D6 04 9E F6 AE 4E 04 2E A6 1E 2E 04 B6 A6 CE CE 86 E6 A6 CE 74 04 2A 16 A6 04 76 A6 1E 2E 04 66 36 86 E6 04 96 CE 04 8C 26 0C EE 86 2E CC 4E C6 0C 36 0C 4E AC 74
Obviously being hexadecimal, we attempted to convert the string to ASCII. Unfortunately, this resulted in a string of nonsense. Ultimately, we were able to decipher this message, largely thanks to Jon's work in the car on the ride home. However, working on this level took the most of amount of time in this entre crypto challenge.
During the hours of discussion about this puzzle, at some point we decided to do a DNS TXT record query on oldgregg.wtf to see whether @lintile had hidden any hints for us. Fortunately, that suspicion was correct:
dig oldgregg.wtf TXT
oldgregg.wtf TDk6IHJldmVyc2UgdGhlIGJ5dGVzISAK
We suspected that the string in the TXT record was base64 encoded. Using the base64 decoder on that string resulted in the following:
L9: reverse the bytes!
We suspected this hint meant that we needed to reverse the bits in each byte of the hexadecimal string provided in order to proceed to level nine. The method to perform the necessary reversal began with converting each byte in the given message to binary. We'll start with the first byte, 2A:
0010 1010
Reversing the bits yielded the following byte:
0101 0100
This site was a great resource to accomplish this task:
https://www.binaryhexconverter.com
Converting the binary representation back to hexadecimal gave us the hex value 54. We could then replace all instances of 2A in the original message with 54:
54 16 96 CE 04 F6 76 A6 04 B6 86 9E 04 16 86 6E A6 04 46 A6 A6 76 04 16 86 4E 26 04 2E F6 04 26 F6 34 04 46 AE 2E 04 2E 16 86 2E E4 CE 04 EE 16 9E 04 9E F6 AE 04 86 36 EE 86 9E CE 04 C6 16 A6 C6 D6 04 9E F6 AE 4E 04 2E A6 1E 2E 04 B6 A6 CE CE 86 E6 A6 CE 74 04 54 16 A6 04 76 A6 1E 2E 04 66 36 86 E6 04 96 CE 04 8C 26 0C EE 86 2E CC 4E C6 0C 36 0C 4E AC 74
Once a bit-reversal had been completed for all bytes in the message, the ASCII character for each of the hex values was retrieved from an ASCII Table:
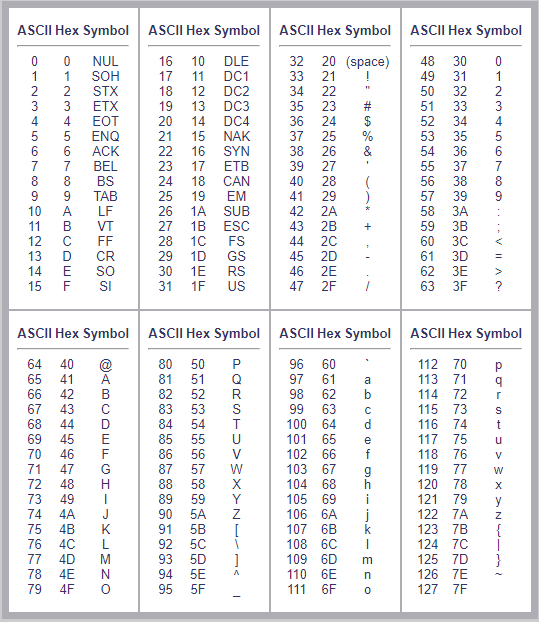
When that was done, we had the following message:
T h i s o n e m a y h a v e b e e n h a r d t o d o , b u t t h a t ' s w h y y o u a l w a y s c h e c k y o u r t e x t m e s s a g e s ! T h e n e x t f l a g i s 1 d 0 w a t 3 r c 0 l 0 r 5 !
We were then able to proceed to Level 9 by submitting the following URL:
https://oldgregg.wtf/9/41fa577c-687b-4b5d-af35-50396b070fda/1d0wat3rc0l0r5
Level 9:
The level nine page provided the following message for us:
FILBALCWUDCHCHCAGUEVAIZCIQGUPHHFYSARCLKQTGNTTUWGCLAAKZ
The length of the string is 54, which is even, and frequency analysis showed us that letters J, M, O, and X are not represented in the message. Given that information, it's reasonable to suspect that the Playfair Cipher was used to produce the message text.
The Playfair Cipher is a keyed cipher. Although we were not provided a key, it was pretty easy to guess. The theme of the contest was Old Gregg, so "oldgregg" was a reasonable, and correct, guess for the key. Using that key, the message text deciphered to the following:
ANDALWAYSREMEMBERTOPLAYFAIRTHENEXTFLAGISMYMUSTYLAGOONX
We were then able to proceed to the final level using this URL:
https://oldgregg.wtf/10/41fa577c-687b-4b5d-af35-50396b070fda/mymustylagoon
Level 10:
The only content on the final level page was a link to a ZIP file:
This is a password-protected ZIP file that contains a single file: morsecode.wav. In order to extract the WAV file, the correct password must be provided. Since "oldgregg" was the key in the last level, we figured that would be good to try. Fortunately, that worked, and we were able to retrieve the WAV file:
Decoding the morse code revealed the following message:
THE LAST TASK IS SIMPLE FIND LINTILE AND PERFORM YOUR FAVORITE SCENE FROM THE MOVIE HACKERS FOR HIM YES THIS IS SERIOUS IT IS FOR A HUNDRED DOLLARS
