InfoSec | Crypto Challenges | CarolinaCon 2019
Although we decided to attend CackalackyCon in 2019, we found that the Crypto Challenge from CarolinaCon 15 was still online. We decided to work on the CC15 challenge while attending CackalackyCon. The CC15 Crypto Challenge was available (and still is as of February 2022) at https://crypto.carolinacon.org/
The journey began with this welcome page:
Level 1:
This challenge began with a combination of ciphers. The first step in deciphering this message is to use the Letter-Number Cipher:
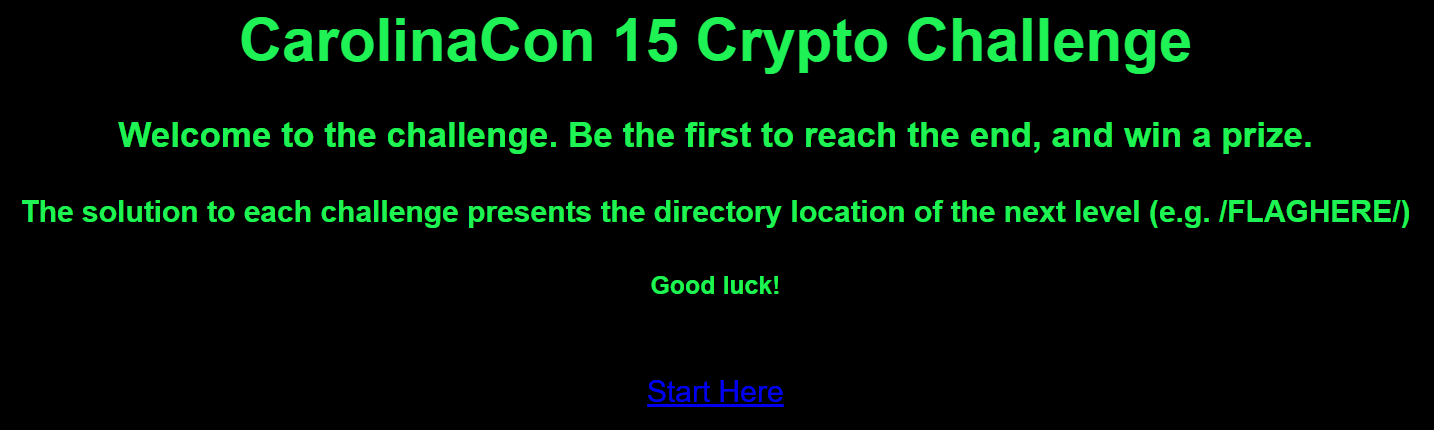
12 21 21 7 12 26 8 12 15 18 23 8 7 26 9 7
becomes
LUUGLZHLORWHGZIG
As previously mentioned, this used a combination of ciphers, so further work is needed to reveal the actual message. This can be deciphered using Atbash:
OFFTOASOLIDSTART
So we were able to proceed to the next level by submitting this url: https://crypto.carolinacon.org/OFFTOASOLIDSTART
Level 2:

For this level we were presented with two pieces of the puzzle: the message and the key. The message was provided in the line at the bottom:
BZRFT SLDXR CSFSE OBC
This message is encoded using the Playfair cipher. Fortunately, the keyed alphabet was also provided, and we did not have to make any guesses:
C A R O L
I N B V W
Z Q H K M
Y S G D U
T E P F X
Using this information, we were quickly able to decipher the message:
IHOPEYOUPLAYEDFAIR
We proceeded to Level 3 using the same type of URL submission previously used.
Level 3:
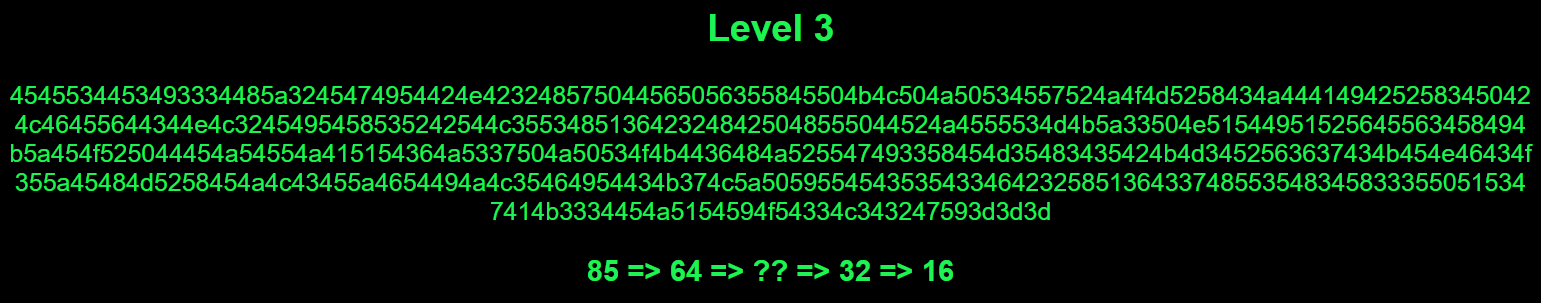
This level presented us with an encoded string and a hint at the bottom. The hint provided us with a series of base encoding types, with one missing, used to encode the message. In order to decode the message, we must work backwards through that series, and discover what the missing type is.
The encoded message string is:
4545534453493334485a3245474954424e423248575044565056355845504b4c504a50534557524a4f4d5258434a4441494252583450424c46455644344e4c
3245495458535242544c3553485136423248425048555044524a4555534d4b5a33504e51544951525645563458494b5a454f525044454a54554a415154364a
5337504a50534f4b4436484a525547493358454d35483435424b4d3452563637434b454e46434f355a45484d5258454a4c43455a4654494a4c35464954434b
374c5a50595545435354334642325851364337485535483458333550515347414b3334454a5154594f54334c343247593d3d3d
The last type noted in the hint is 16, so we began with a hexadecimal (Base 16) decode:
EESDSI34HZ2EGITBNB2HWPDVPV5XEPKLPJPSEWRJOMRXCJDAIBRX4PBLFEVD4NL2EITXSRBTL5SHQ6B2HBPHUPDRJEUSMKZ3PNQTIQRVEV4XIKZEORPDEJTU
JAQT6JS7PJPSOKD6HJRUGI3XEM5H45BKM4RV67CKENFCO5ZEHMRXEJLCEZFTIJL5FITCK7LZPYUECST3FB2XQ6C7HU5H4X35PQSGAK34EJQTYOT3L42GY===
Working backwards, the next type in the hint is 32, so we then performed a Base 32 decode:
!$9#|>tC"aht{<u}{r=Kz_"Z)s#q$@c~<+)*>5z"'yD3_dxx:8^z<qI)&+;{a4B5%yt+$t^2&tH!?&_z_'(~:cC#w#:~t*g#_|J#J'w$;#r%b&K4%}*&%}y~(AJ{(uxx_=:~_}|$+|"a<:{_4l
At this point, we arrived at the missing step in the hint. There appeared to be several invalid characters for the message to be encoded in a different base. We eventually discovered that the characters needed to be encoded, using ROT47, in order to proceed:
PShRMmErQ29ELkFNLClzK0Q+XDRBS1o4OkZXYmdKQVJsb05IIig/KkBxXUZjL2cqdTJEZSE/aUEwPnU0K0VWOi4rRHRiOEY8R0MyRyVHSjRCT3UzcTNYUTNJOWpyLWFII0liO0NMS1ZMQ2kiL0c=
Continuing with the hint series, the performed a Base 64 decode to get these characters:
=(Q2a+CoD.AM,)s+D>\4AKZ8:FWbgJARloNH"(?*@q]Fc/g*u2De!?iA0>u4+EV:.+Dtb8F<GC2G%GJ4BOu3q3XQ3I9jr-aH#Ib;CLKVLCi"/G
Then the final step was to perform a Base 85 decode, to get the message:
Well done. I hope you used Cyberchef. Proceed to the next level here:
/MatryoshkaDolls/
Level 4:
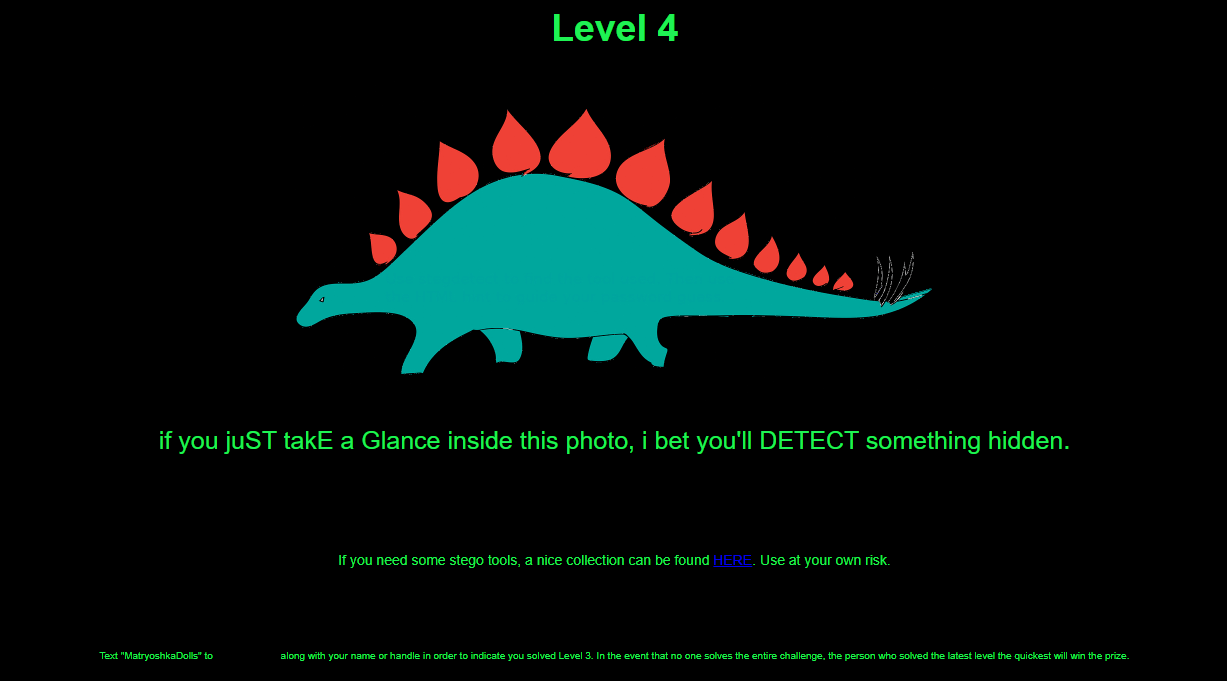
The hints on this page made it very clear that we'd be working on an image steganography challenge:
- The image of a stegosaurus
- The capital letters in a sentence of otherwise lowercase letters (STEGDETECT)
- The reference to "stego tools"
- The link to SSAK on github.com
The image of the stegosaurus was the obvious place to check for steganography:
We used StegDetect to detect the type of steganography used in the image: F5 JPEG. Unfortunately, the second set of tools referenced in the hint (SSAK) weren't very useful. We were able to use jpseek, with the password carolinacon, to extract the hidden image. The image displayed the following text:
Congratulations on finding the
flag! Please proceed to the next
level of the challenge:
/FoundThatWhichWasHidden/
Level 5:

We immediately found this interesting, since it appeared to employ a Playfair cipher, but there were two keyed alphabets presented. Being unable to produce anything meaningful through Playfair deciphering with either keyed alphabet, we searched for clues. The @CarolinaCon Twitter feed provided a helpful hint with this tweet:
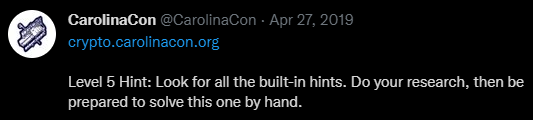
https://twitter.com/CarolinaCon/status/1122331283001106432?s=20&t=52EEBBPHLScDe8kVxXUhXw
The hint indicated that there was definitely a clue hidden somewhere, so we checked the first obviously place: the page source for level 5. A clue was quite prominently displayed within the source:
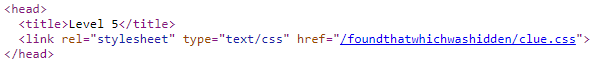
The clue.css (download: original / mirror) file contained two helpful hints:
@import '/foundthatwhichwashidden/hint.css';
/* The NSA has something to say about this cipher */
The second hint file, hint.css (download: original / mirror), also contained a helpful hint:
/* Charles David knows great detail about this cipher */
Knowing that the NSA and Charles David were related to the cipher used for this level, we found a document hosted by the NSA which described the cipher:
Mirror: https://www.belthasar.com/infosec/crypto-challenges/carolinacon-2019/world_war_II.pdf
The information in the document, specifically on pages 5 - 7, revealed that the cipher used for level 5 was a German Army field cipher used during World War II. The Germans called it Doppelkastenschlüssel, or in English: Two-Box Cipher. The Allies referred to it as the Non-Indicator or NI cipher.
An enciphered comment on Twitter also attempted to provide a clue:
Xiovfy Zucl
Deciphering using ROT6 revealed:
Double Fair
However, attempting to decipher the message using the Double Playfair, or Two Square, method had not been successful, so we ignored this and used the information authored by Charles David.
Using that information, we were able to get the following message from the cipher text:
BROKETHECODE
Level 6:
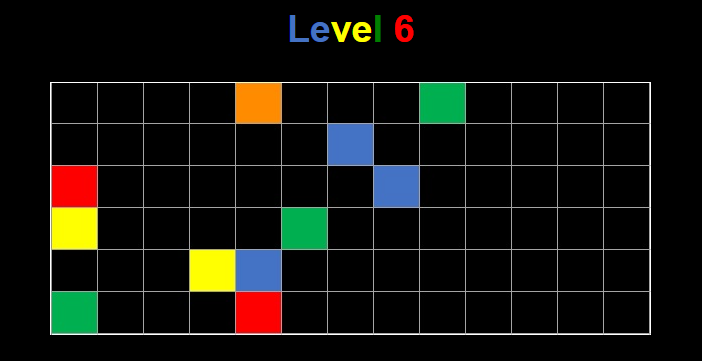
Level 6 presented us with an interesting collection of information graphically:
- The characters of "Level 6" using different colors
- A 6 x 13 matrix
- Some elements of the matrix being one of five colors
This information indicated that there was a relationship between the characters in the title and the elements in the matrix. However, since it was an image, we decided to look for traces of steganography. Finding none, we proceeded to examine the image and how it might relate to the characters in the title.
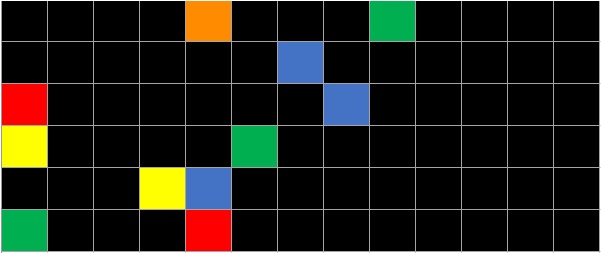
We noticed that each row had 13 columns, which meant that the English alphabet, 26 letters, would occupy two rows. We then thought that the colored elements in the matrix could indicate significant letters in an alphabet. But, there were six rows containing 78 elements, which is far more than the 26 letters of the alphabet. The last hint left on Twitter confirmed our next thought: that the letters repeat in the matrix:
https://twitter.com/CarolinaCon/status/1122331393743310848?s=20&t=52EEBBPHLScDe8kVxXUhXw
By this point, all of this seemed incredibly familiar. I was certain I'd read about this sort of cipher previously, and a few searches on the Internet confirmed my suspicion; this was a Grille Cipher!
Knowing this, we added letters to the image of the matrix:
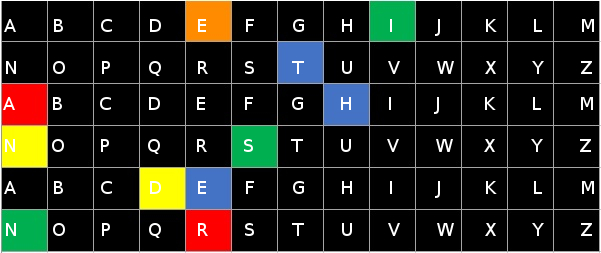
Using this image, we were able to determine the letters of interest based on which elements were color-filled:
| Color | Letters |
|---|---|
| Orange: | E |
| Green: | I S N |
| Blue: | T H E |
| Red: | A R |
| Yellow: | N D |
All of the letters of interest were:
E I S N T H E A R D
Seeing THE present, we thought this may be an anagram. After reviewing some possibilities, we realized we were most likely missing a letter. After trying some possibilities, we realized that there were only four colors in the title text: blue, yellow, green, and red. However, there were five colors in the matrix: blue, yellow, green, red, and orange. Since orange is a combination of yellow and red, we thought that might indicate the letter in that element would be used twice. Since the letter in that element was E, we added another to the set of letters:
E I S N T H E A R D E
After that was done, an anagram using all of the letters was produced:
THEENDISNEAR
Going to the URL https://crypto.carolinacon.org/TheEndIsNear produced the following message:
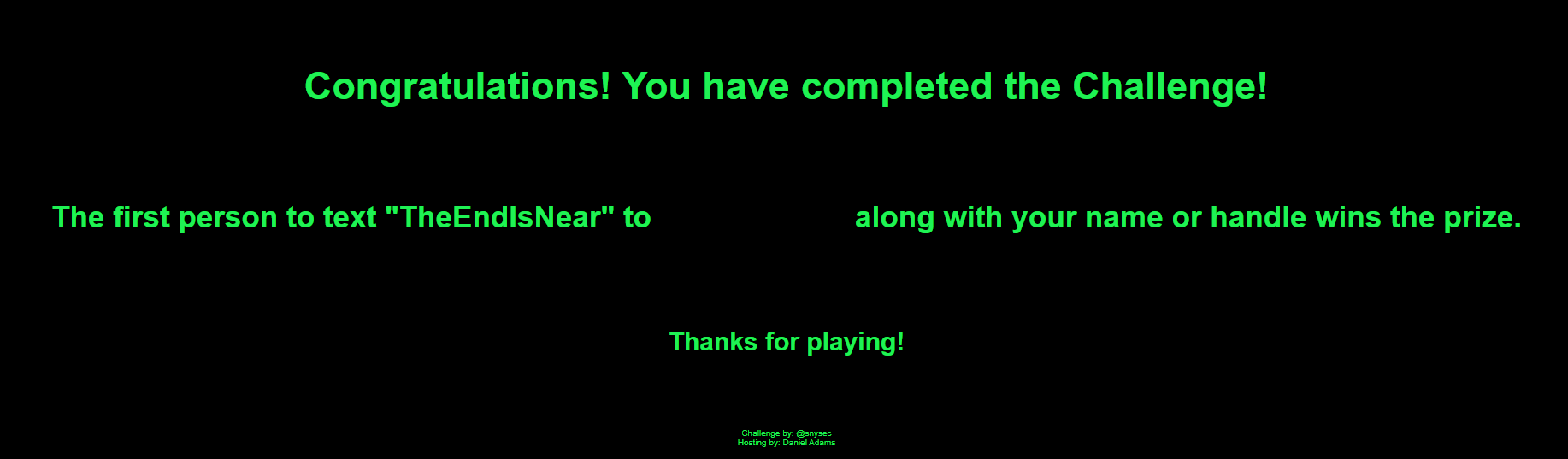
Although we completed this challenge a few weeks late, we decided to send a message to the number provided and inform them that we'd completed it. I quickly received a response via Signal from Vic Vandal, who organized CarolinaCon, and had a nice chat with him.
